|
Size: 4115
Comment:
|
Size: 4349
Comment:
|
| Deletions are marked like this. | Additions are marked like this. |
| Line 6: | Line 6: |
| Line 14: | Line 13: |
| Time used:: | Time used:: <<BR>> |
| Line 17: | Line 16: |
| Time estimated:: | Time estimated:: <<BR>> |
| Line 20: | Line 19: |
| Line 23: | Line 21: |
| Line 30: | Line 27: |
| Line 32: | Line 28: |
| Line 38: | Line 31: |
| Components: * Doms auth checker: Service for checking credentials against the policy in doms. Author IT Digitale Ressourcer * IP2RolesMapper: Service for mapping user ip to a set of roles. Auther Unknown. * URL2FileMapper: Service for mapping a permament url to a file. Authro IT Drift * PHP main app: Service for handling the flow between the services. Auther IT Service * Apache server: Server for housing the php app, and handling the perm urls. Use URL_rewrite to forward requests to php. |
|
| Line 40: | Line 40: |
| 1. This apache server has the nessesary rewrite filters set up to forward the request to a php application. 1. Php application ('''Written by IT service''') 1. Extract Wayf credentials from the user. There might be no credentials, which is not yet an error. 1. Extract the user IP (or domain), and set this as a user property 1. Call the DomsAuth service with the permanent URL and the credentials if any (and the IP property), ('''Written by IT Digitale Ressourcer''') 1. Doms Auth lookup the corresponding file object in fedora, and attempts to read this with the supplied credentials. If succesful, true is returned. Else false. 1. If the DomsAuth service gave false and the user had no WAYF credentials, redirect the user to a wayf login page. 1. If the DomsAuth service gave false, but the user had WAYF credentials, report error. 1. If the DomsAuth service gave true, stream the file through the php app to the user 1. Stream app. This app streams the given file from whereever into the php script so the user can read it. ('''Written by IT Maintenance''') |
|
| Line 51: | Line 41: |
| It can be seen that the php app will become a bottleneck. There are several designs that could work around this. Having several identical apache servers, and using a round robin dns would split the load. | User GETs a perm url 1. Apache -> url_rewrite the requests and forward it to php app 1. Php application 1. Invoke IP2RolesMapper to get user roles. 1. Invoke Doms Auth Checker(url, roles) to see if the IP roles are enough to get the file 1. If no: 1. Extract Wayf credentials from the user, by redirecting him to the WAYF page. 1. Invoke Doms Auth Checker(url, creds) to see if the file is assesible with the creds 1. if no: 1. Send Unauthorized error 1. Invoke URL2FileMapper to get a file location. 1. Open this file. 1. (Request file mime-type from Fedora) 1. Stream it to the user. |
| Line 53: | Line 56: |
| It can be seen that the php app will become a bottleneck. There are several designs that could work around this. Having several identical apache servers with identical php apps, and using some sort of load balancing would work. | |
| Line 54: | Line 58: |
| === IP Roles are enough === | |
| Line 55: | Line 60: |
| {{attachment:auth2.jpeg}} === Wayf creds needed === {{attachment:auth1.jpeg}} === No creds good enough === {{attachment:auth3.jpeg}} |
|
| Line 60: | Line 74: |
Task Doms Auth system
- Title
- Doms Auth system
- State
- Not started
- Time used
- Time estimated
Description
The doms auth system is responsible for ensuring that no user can access files without sufficient credentials. Furthermore, no doms record should be viewable without the nessesary credentials. These are two different requirements.
- Auth check on bitstorage access
- Auth check on long post viewing
Bitstorage auth design
This design has been worked out between Mads (INITIALS), Per (INITALS) and abr. Jhlj has been informed of some of the design, but need to sign of on the final version.
The design is as follows:
Components:
- Doms auth checker: Service for checking credentials against the policy in doms. Author IT Digitale Ressourcer
- IP2RolesMapper: Service for mapping user ip to a set of roles. Auther Unknown.
- URL2FileMapper: Service for mapping a permament url to a file. Authro IT Drift
- PHP main app: Service for handling the flow between the services. Auther IT Service
- Apache server: Server for housing the php app, and handling the perm urls. Use URL_rewrite to forward requests to php.
- Each file in bitstorage is assigned a permanent URL
- An Apache server is set up to handle these URLs
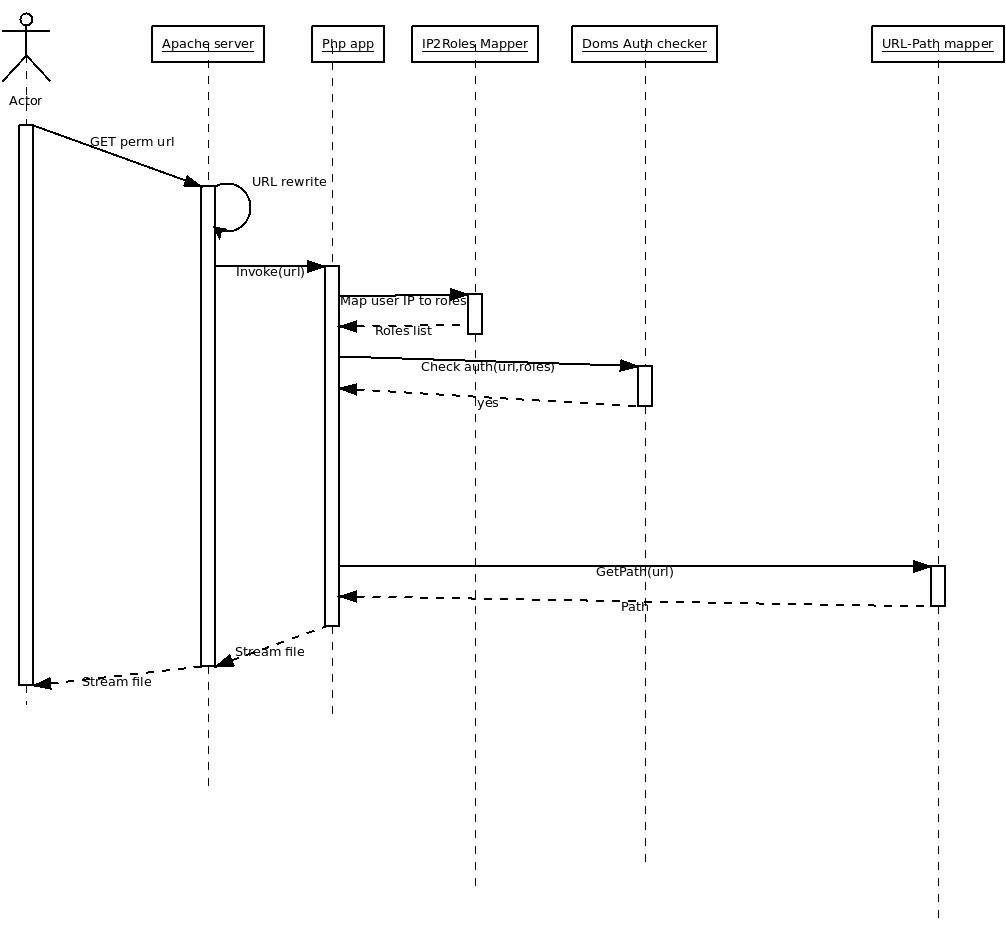
User GETs a perm url
Apache -> url_rewrite the requests and forward it to php app
- Php application
- Invoke IP2RolesMapper to get user roles.
- Invoke Doms Auth Checker(url, roles) to see if the IP roles are enough to get the file
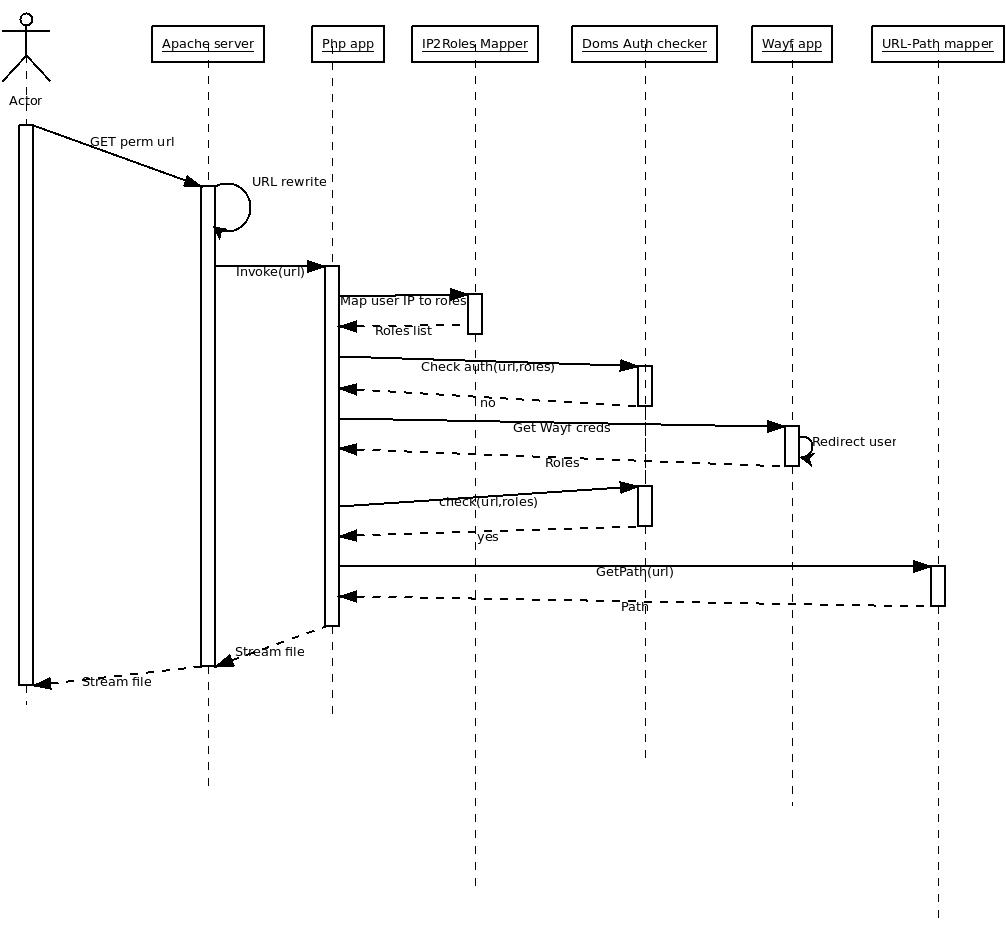
- If no:
- Extract Wayf credentials from the user, by redirecting him to the WAYF page.
- Invoke Doms Auth Checker(url, creds) to see if the file is assesible with the creds
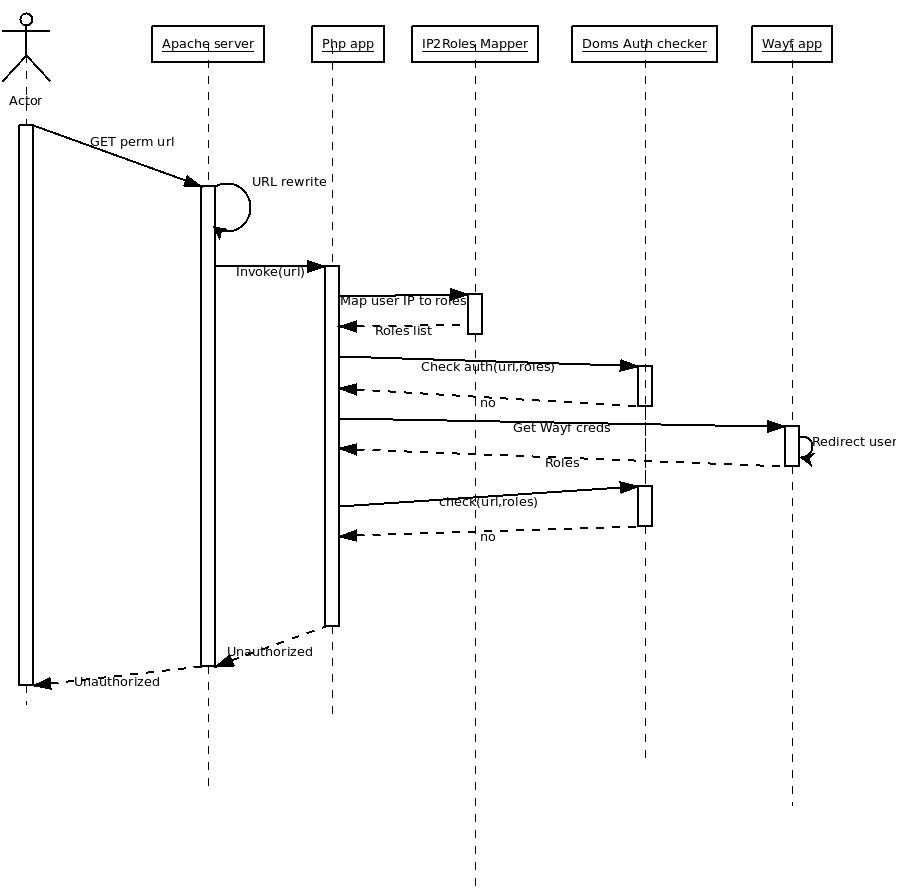
- if no:
- Send Unauthorized error
- Invoke URL2FileMapper to get a file location.
- Open this file.
- (Request file mime-type from Fedora)
- Stream it to the user.
It can be seen that the php app will become a bottleneck. There are several designs that could work around this. Having several identical apache servers with identical php apps, and using some sort of load balancing would work.
IP Roles are enough
Wayf creds needed
No creds good enough
Sub tasks
| Title | State | Time used | Time estimated |
Documentation
Progress history
| Iteration | Time used | Status | Notes | Tasks adressed |